
Mobility Solutions- Driving the Future of Business
In a world where people are constantly on the move, businesses must keep up. Enter mobility solutions" the technologies that enable people to work, connect, and interact with systems and services from anywhere, at any time, using mobile devices.
Whether you're a startup, a logistics company, or a global enterprise, mobility is no longer optional" it's essential.
What Are Mobility Solutions?
Mobility solutions refer to the technologies, services, and strategies that allow seamless access to business processes and information through mobile devices such as smartphones, tablets, laptops, and wearables.
They often include:
Mobile apps
Remot..... Read More

Harvest Now, Decrypt Later
Why Quantum Threats Demand Action Today
When we think about cybersecurity threats, we usually imagine things happening in the moment—phishing scams, ransomware attacks, or high-profile data breaches making headlines. But there’s another threat quietly unfolding in the background. It’s subtle, slow-moving, and potentially far more damaging: “Harvest now, decrypt later.”
At first glance, it sounds like something out of a sci-fi novel. But it’s very real. The idea is this: attackers are actively collecting encrypted data today, knowing they can’t crack it yet, but betting that one day, thanks to advances in quantum computing, they will.
And that changes the ..... Read More

Latest in Data Breaches
Credential Stuffing Attacks- What They Are and How to Stay Safe?
In today’s digital age, cyber threats are evolving faster than ever, and one particularly dangerous attack method that continues to make headlines is credential stuffing. Although it might sound like something from a tech thriller, it’s a very real threat that affects individuals, businesses, and even large organizations across the globe.
What Is Credential Stuffing?
At its core, credential stuffing is a type of cyberattack where stolen usernames and passwords—often obtained from data breaches—are used to gain unauthorized access to user accounts on..... Read More
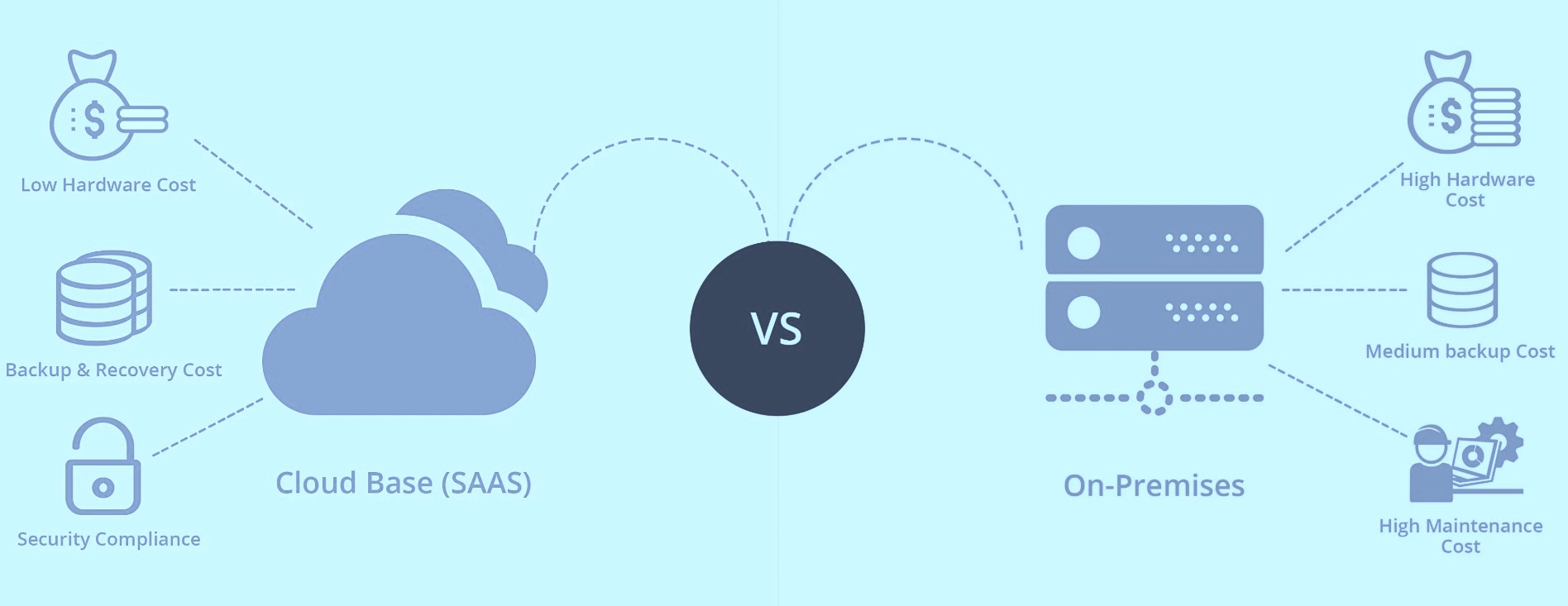
Backup Strategies
SaaS vs. Traditional IT Infrastructure— What You Really Need to Know
We’ve all heard the advice: “Make sure to back up your data.” It sounds simple enough—but in practice, crafting an effective backup strategy is anything but straightforward.
Whether you run a growing startup, manage IT for a large enterprise, or handle tech decisions for an SMB, how you back up your data and where that data lives makes a huge difference.
SaaS platforms and traditional IT setups aren’t built the same way. And if your backup strategy doesn’t account for that, you could be in for a rude (and costly) surprise.
Let’s break this down so you know exactly w..... Read More